By Brenton Spencer, Support and Delivery Specialist
Have you ever opened your email to find a message from a coworker that seems suspect? Have you received a OneDrive link or password reset from Microsoft that you did not request? Or have you ever received an email that was sent from your own email address, but you did not send it? Chances are that someone is using your companies or your email address to gather information in a phishing attempt.
Above are examples of email spoofing. More than 90% of cyber-attacks start with an email, there are roughly 3.1 billion spoofing & phishing emails sent daily, and email spoofing & phishing have had a worldwide impact costing an estimated $26 billion since 2016. With these cyber-attacks becoming so commonplace I would like to highlight a few of the top ways you can fall victim to a phishing scam.
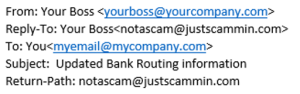
Intra-Org / Self-to-self spoofing
![]()
Intra-Org or self-to-self spoofing is where your organization’s domain user addresses are spoofed for the purpose of phishing or scamming someone. This may come in the form of an email from a coworker with an attached PDF, an email from a boss asking you to purchase gift cards, or an email from yourself with a Sharepoint link. If an email is sent from and shows a display name of someone that is familiar, users are more likely to trust the message. All these examples have the same goal: to deceive users and trick them into performing the phisher’s desired action.
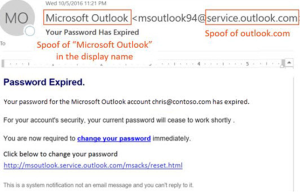
External Spoofing
Cross-Domain or external spoofing is where a message is received from outside your organization that prompts a response or call to action. These messages are sent to solicit a response such as clicking on a link, replying to an email, or opening an attachment to either gather information or install programs. The display name & address that are sending the message appear to be from a legitimate service or sender (such as Microsoft, Adobe, Apple, etc), and appear as legitimate email requests for account management.
For example:
How do they do it?
Email spoofing does not require any sort of advanced system or detailed tech knowledge to complete. Spoofing emails are created by the spoofer adjusting email message headers. By adjusting these email message headers, the phisher is able to adjust the sending address, the reply-to address, email return path, or anything else they can to trick you into believing the message is legitimate. When analyzing the message details & headers, the received message details will show that the message was not sent from a trusted sender, but from a suspicious source.
How is it prevented?
Preventing spoofed emails from being opened or acted upon requires a mix of user training and email security standards. SPF, DKIM, and DMARC email security standards can be utilized to prevent the messages from being received.
- SPF – outlines valid IP addresses that are approved to send emails for a specific domain.
- DKIM – Prevents spoofing emails from being sent as outgoing messages on your domain. DKIM updates the DNS entry of an email domain to add a digital signature to the message header and to ensure that the email remains unaltered from when it was sent.
- DMARC – An email authentication, reporting and policy protocol that uses both SPF and DKIM to provide information about the email domain.
- Cybersecurity Awareness training – One of the most important factors in preventing spoofed emails from being acted upon is user training. Having users that are suspicious of emails and can recognize flags of spoofed emails/phishing emails. Some of the most common flags are:
- use of poor language, grammar, and punctuation.
- use of language that conveys a sense of urgency
(call to action). - mismatching or inaccurate information in the
“from” field. (For example, does the sender’s name match their email address?) - Domain information that is incorrect (is there an extra letter in the sending domain? Was a letter replaced with a number?)
As phishers become more creative with their attempts to gather information, it is important to diminish the possible attempts in every way possible. Mitigating these attempts through security standards & user training reduces the possibility of confidential data loss, installation of malicious software, and financial loss.
Atom Creek is the expert in making sure you and your company stays safe. If you could benefit from employee training or an update to your security posture please contact us today.


